Cryptography
- Tanha Patel

- Jul 1, 2019
- 3 min read
Updated: Feb 11, 2021
When it comes to hiding about the securing the data there are three basic types of secure system by which we can protect or secure our data. Those are Cryptography, Stenography and Perturbation technique. so today i am going to explain cryptography in brief.

First of all let's talk about the meaning of the word cryptography the prefix "crypt" means "hidden" and the suffix "graphy" means "writing". Cryptography is basically a way of protecting data over network so that no third party can access that. More generally, cryptography is about constructing protocols that cannot be accessed by third parties or the public. In the Modern Era Cryptography is synonym to Encryption. The Security level of a cryptograph is usually determined by the Type of Encryption and its key.

Key: The cryptographic message or data can only be unlock by the Key, The Key possess very high level mathematics and complex algorithms. The key generation and digital signing and verification is helpful to protect data privacy, web browsing on the internet and confidential communications such as credit card transactions and email. So let’s talk about the keys for cryptography. There are 3 types of Key or Methods for Cryptography

Single Key
Public Key
Hash Functions
1. (Single Key/Symmetric): Same Key is used for encryption and decryption. This key usually uses a algorithm which is symmetric. This method is way faster than the public key method. The security of this is directly proportional to the size of the key.
A 6 bit key has 64 combinations, and a 7 bit key has 128 combinations. so it is difficult to break these kinds of Encryption.

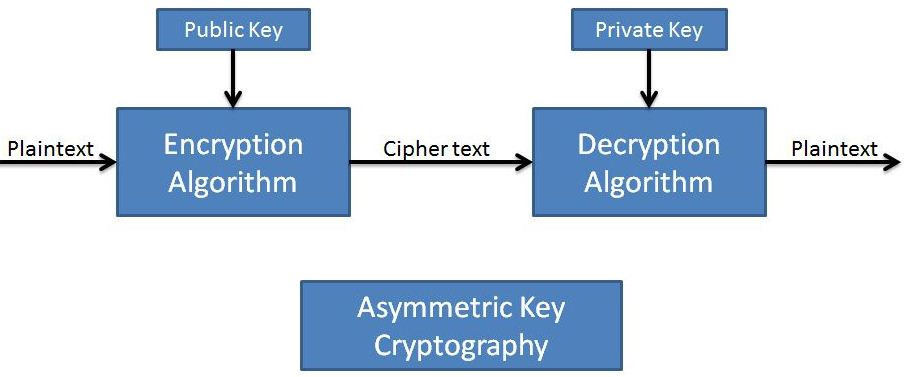
2. (Public Key/Asymmetric): Different Key is used for Encryption and Another different for decryption. In this method usually one is a public key and second is a secret key. The process for decrypting these keys is much slower as compared to Single Key.
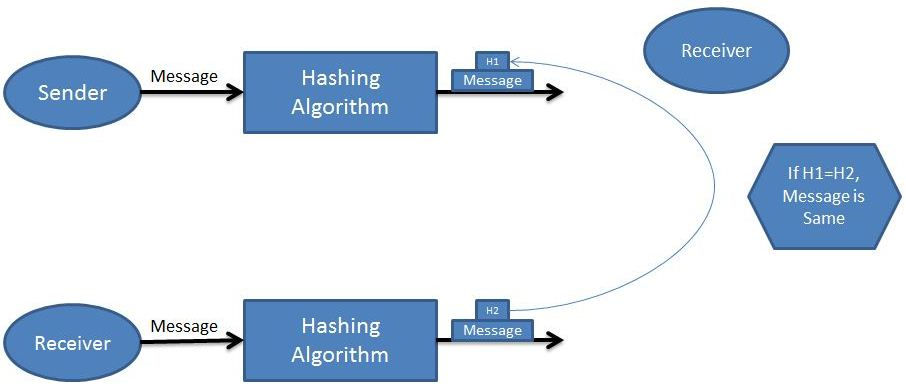
3.Hash Function: In this there is no key for decryption. The plain text or message is converted to the hash value using hash functions. The plain text can be obtained by when Both the Hash value at Receiver and sender ends matches.
Cryptography can be done using things like hiding text into images, Stenography and using algorithms. The most common way to make cryptography is using different type of ciphers which converts Plain text into rubbish which doesn’t make any sense. Ciphers such as Substitution ciphers, Book ciphers etc.
Benefits Of Cryptography:
Confidentiality: the information can only be understood by one for whom it is intended
Integrity: The Information cannot be manipulated in storage or during transits from sender to receiver. In case if someone tries to alter it an alteration will be detected
Non-repudiation: At a later stage the receiver and the sender cannot deny about the intention of transits of information.
Authentication: The sender and receiver can verify each other’s identity and the Source of Information
The System Fulfilling all these four Qualities is consider is cryptosystem and people working with Cryptography are called Cryptographer. In a crypto system not only the mathematical algorithm but also human behavior is very important like hard to guess passwords and logging off unused system.
Disadvantages:
Well In our World of Cyber security It doesn’t matter what level of security you are using for protection of system and all. Everything is always vulnerable at some point so is this
Very securely encrypted, digitally signed information can be very difficult to a genuine user at crucial time. This process takes a lot of time Hence it can be a trouble for you sometimes
Cryptography cannot save you, if you are using a vulnerable system with poor protocols, design and procedure.
If the key is not built properly It is vulnerable to brute force attack. The attacker will try some random combinations and boom! your personal messages and data are no more personal.
Future of Cryptography:
Elliptic Curve Cryptography (ECC): In ECC one can create cryptograph of same Security level but in a much lesser time. ECC is going to save a lot of time at both the end, but its advantages and disadvantages are still not clear. Hence it isn’t coming into practice right now.

Quantum Computation: Our normal computers store data in the form of bits or you can sat in the form of "1" and "0" but in the QC the data will be stored in the form of “ qubits”. It will store data using quantum superimposition of multiple states. Hence it will increase the computation speed on processors which will reduce the time for decryption.
Well That's it from my side about Cryptography. Hope you like it..








Comments